I recently switched my primary mouse from a Logitech V450 to a much simpler Logitech RX650. The RX650 is a basic OEM mouse. It is larger than the V450 and doesn’t have the useful space below the mouse to store the compact USB receiver. It only has a range of 1.5m from the receiver, compared to 10m for the V450. So why did I switch? Because the RX650 uses 27 MHz for communication, whereas nearly every other cordless mouse on the market today, including my old V450, uses 2.4 GHz.
You are currently browsing the yearly archive for 2009.
Firefox has a very annoying “feature” – it remembers any HTTP authentication tokens for as long as Firefox remains open. Any by “open”, I mean “the browser is running”, not “the tab/window is open”.
Why is this bad? For several reasons. Read the rest of this entry »
Although I administer most servers via SSH, I also use Webmin. Webmin is convenient for almost any simple administrative task, and is often better for some jobs. For instance, it is the easiest way I have found to browse Postfix email queues. Perhaps most importantly, it can save you from having to learn yet another daemon’s unique configuration language and syntax.
It can also be very handy if you have to fix something from your smartphone, where the command line isn’t always the best choice of tool. Enter: the Virtualmin Mobile/iPhone Theme.
Tags: webmin
You really shouldn’t allow SSH logins via password. This is doubly true for root. On most of my hosts we allow SSH for normal users with a password, but restrict root to SSH keys only. And we always protect against brute force attacks with fail2ban.
If you aren’t already using SSH keys and SSH agent, you should. SSH agent forwarding allows for secure sideways authentication. For example:
Cleaning up after the KDE 4 upgrade continues. Today I tried to port kregexpeditor from hardy, but pbuilder stopped with a library conflict:
kdelibs5-dev: Conflicts: kdelibs4-dev but 4:3.5.10.dfsg.1-1ubuntu8 is to be installed
I’m sure I could have resolved this, but I decided to test the hardy package before spending any more effort. The package installed without complaint, and the binary runs. I’ve added the amd64 and i386 packages from hardy-backports to the repo for jaunty.
Until last week I still ran Kubuntu 8.04 (Ubuntu with KDE) on my personal desktop. We also use this on all our corporate desktops, and my wife’s PC at home. I wanted to wait for KDE 4 to mature a bit more before upgrading, so intrepid wasn’t an option.
I waited 4 months after the release of jaunty, so the problems should be either documented or resolved, and the release notes didn’t mention anything that seemed too serious. So I decided to give it a test.
In the last 3 weeks our company mail servers have been slammed with a massive increase in spam relay attempts. Logs showed many failures like so.
Jul 12 14:15:26 mailserver.example.com postfix/smtpd[19885]: NOQUEUE: reject: RCPT from 206.12.0.10.in-addr.arpa[10.0.12.206]: 554 5.7.1 <symons@yahoo.co.uk>: Relay access denied; from=<yyjaqveh@lpsb.com> to=<symons@yahoo.co.uk> proto=ESMTP helo=<206.12.0.10.in-addr.arpa>
IP addresses have been obscured to protect the guilty (or ignorant, as this is certainly a botnet). Unfortunately, a large number of the IP addresses in question belonged to my own satellite customers. Mail servers for our other domains were almost entirely unaffected. Which tells me that some bastard has written a botnet spam client that looks up its own public IP, finds the reverse DNS entry, looks up the MX record of the corresponding domain, and then attempts to relay mail through that server. This is particularly mean, as it will encourage your own ISP to shut you down.
Tags: networking, security
After my recent adventure with reverse-path filtering, I didn’t expect to see it again so soon. And then I took another look at a long-standing annoyance in our OpenVPN network.
I set up OpenVPN so our offices and laptops could securely access internal resources. This lets me print documents directly to another office, for instance. Or access web-based applications that we don’t make available to the public. Or remotely SSH into a PC and fix a problem. Read the rest of this entry »
Tags: kernel, networking, openvpn
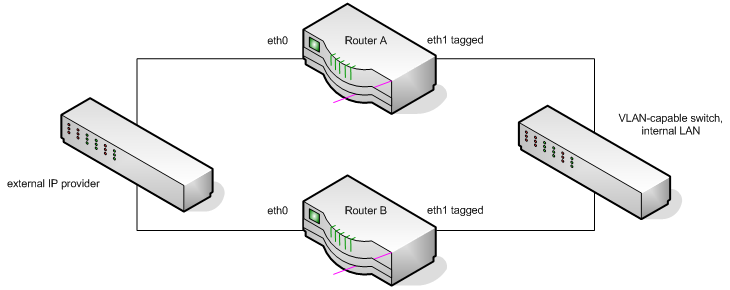
I recently created a very complex network using routers running Ubuntu Hardy. These routers were configured with the following features:
- failover shared IP addresses using heartbeat
- routing announcements via Quagga BGPd
- 802.1q VLAN tagging
- multiple physical interfaces
During debugging of this network, I encountered an odd scenario whereby traffic coming in from the external interface (eth0) could not reach the IP address of the secondary (inactive) router’s internal interface (eth1, VLAN tagged).
Tags: kernel, networking
I love SSHFS. I manage a lot of machines, and I very often want to do something like this:
diff root@server1:/etc/randomrcfile root@server2:/etc/randomrcfile
There are ways to do this with Kompare (a KDE diff app) and the fish:// Kioslave, but not on the command line. SSHFS makes it easy:
mkdir /tmp/server1 /tmp/server2
sshfs root@server1:/ /tmp/server1/
sshfs root@server2:/ /tmp/server2/
diff /tmp/server1/etc/randomrcfile /tmp/server2/etc/randomrcfile
I do this so often that I’ve written my own script to handle this for me, smount. Copy it somewhere in your path, remove the extension (or don’t, as you prefer), and optionally make a copy or symlink called “sumount”. Now you can rapidly mount and unmount multiple hosts.






Recent Comments