Late last night, someone began using my home Internet connection in DNS amplification attacks. My Virgin Media cable link was hit with several megabit of “ANY record” DNS queries for ripe.net.
IPs have been changed to protect the innocent.
10 0.004841 23.20.43.112 -> 192.168.1.1 DNS Standard query ANY ripe.net 11 0.004930 192.168.1.1 -> 194.168.8.100 DNS Standard query ANY ripe.net 12 0.005479 194.168.8.100 -> 192.168.1.1 DNS Standard query response DNSKEY DNSKEY DNSKEY DNSKEY RRSIG A 193.0.6.139 RRSIG NS sec3.apnic.net NS sec1.apnic.net NS ns3.nic.fr NS sns-pb.isc.org NS pri.authdns.ripe.net NS tinnie.arin.net RRSIG SOA pri.authdns.ripe.net RRSIG NSEC 256cns.ripe.net RRSIG 13 0.006017 192.168.1.1 -> 23.20.43.112 DNS Standard query response DNSKEY DNSKEY DNSKEY DNSKEY RRSIG A 193.0.6.139 RRSIG NS sec3.apnic.net NS sec1.apnic.net NS ns3.nic.fr NS sns-pb.isc.org NS pri.authdns.ripe.net NS tinnie.arin.net RRSIG SOA pri.authdns.ripe.net RRSIG NSEC 256cns.ripe.net RRSIG
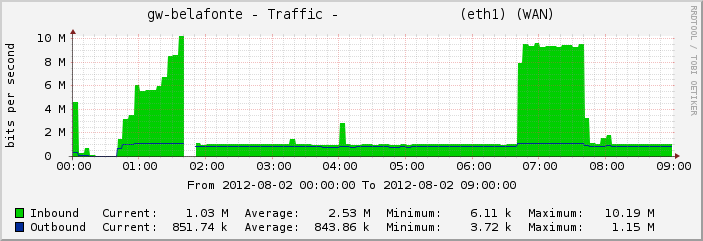
Unfortunately my router’s DNS server then ran the recursive lookup, which caused at least one megabit of sent queries, and raised the total received traffic volume to 10 mbit. It seems that DNS amplification attacks against non-root DNS servers causes as much harm to the intermediate DNS resolver as to the victim.
Somehow the firewall on my OpenWRT router was allowing all incoming traffic to the router itself, even from the outside. I fixed that, and the traffic volume dropped off to just the original 1 mbit of queries.
I assume the script kiddies will let up eventually. If they don’t, I’ll have to deal with Virgin Media tech support. Would someone there kindly change the public IP address of cable modem 00:14:A4:97:5B:FA?
Tags: attacks, networking, openwrt
-
How did you fix the problem as i have the same thing going on right now and I need some help.






7 comments
Comments feed for this article
Trackback link: https://www.tolaris.com/2012/08/02/dns-amplification-attack/trackback/