I acquired an Android-based tablet a few weeks back. After the inevitable period of “new toy!” passed, I started looking into ways to safely archive my data. I already use BackupPC to backup to my PCs, so why not an Android tablet?
I run CyanogenMod 7 on my tablet, which means I have root and the rsync binary. I assume you do too. I also assume you have a working BackupPC installation, and are familiar using SSH key authentication and rsync as a BackupPC transfer method. If not, this is not the time to figure it out. Get it working on a normal Linux backup target first, then come back here.
First, install an SSH server on your Android device. I recommend you use QuickSSHd, but SSHDroidPro works as well. QuickSSHd has a nicer GUI and can run quietly (without persistent notification) in the background. Both are paid apps.
Open QuickSSHd, check “Password”, and enter a password for your root user. Then find the device’s IP address (displayed in the app), and verify that you can SSH in. Assuming its IP address is 192.168.0.100:
ssh root@192.168.0.100
QuickSSHD for Android #
Both QuickSSHd and SSHDroidPro are really just GUIs wrapped around dropbear, so you can (hopefully) trust the cryptography to be implemented correctly. Once you login, verify you have root access, and install your SSH keys.
# id uid=0(root) gid=0(root) groups=0(root) # pwd /data/data/com.teslacoilsw.quicksshd/home # umask 077 # mkdir .ssh # cat > .ssh/authorized_keys
Now paste in your SSH keys. I have one for myself, and one for my BackupPC server:
ssh-rsa AAAABjkkgGSukkA....Yt/Ew== tyler@laptop ssh-rsa AAAABAADsUXeWwh....wkq9F== backuppc@backup-server
And press Ctrl-D to close the file. Finally, set them to be owned by the QuickSSHd app user. This varies between devices, so first find it:
# ls -la /data/data/com.teslacoilsw.quicksshd/home drwxrwx--x 3 app_84 app_84 4096 Jun 2 12:10 . drwxr-xr-x 7 app_84 app_84 4096 Jun 9 17:16 .. drwxrwx--x 2 app_84 app_84 4096 May 29 20:36 .ssh
Here the user is “app_84”, so:
chown app_84:app_84 .ssh/authorized_keys
chmod 600 .ssh/authorized_keys
Now open QuickSSHd, check “Shared keys”, and uncheck “Password” (optional, for enhanced security). You should now see your SSH keys listed by comment in the main app window. If you didn’t change the ownership on the authorized_keys file, they’ll still work for login, but won’t be visible in the app.
In QuickSSHd, Menu / Settings, set the options “Keep Awake” to on, to prevent the phone from sleeping while clients are connected; “Start at Boot” to on; and “Show Notification” to off, so that SSH can run quietly in the background all the time. Contrary to popular belief, a background process on Android doesn’t necessarily consume battery time. A sleeping SSH server does nothing until something tries to connect to it. So your battery is safe, as long as you don’t have a script kiddie roommate, constantly brute-forcing SSH logins against your phone.
Now test that you can login from the “backuppc” user of your BackupPC server. If so, you’re ready to set up this device in BackupPC.
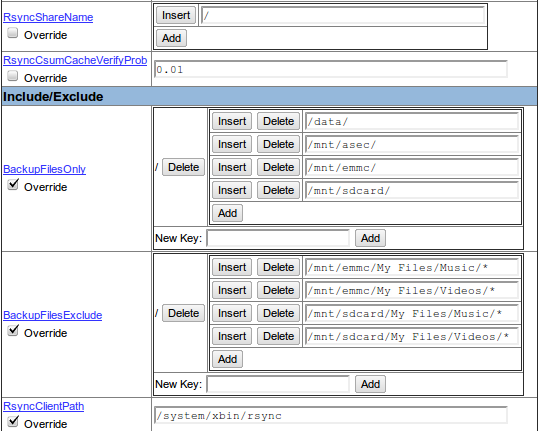
Create a new host, named for your Android device. In the device’s config, go the “Xfer” tab. Set:
- RsyncShareName = /
- BackupFilesOnly = /data/, /mnt/asec/, /mnt/emmc/, and /mnt/sdcard/
- RsyncClientPath = /system/xbin/rsync (may be specific to CyanogenMod, check from the shell first)
- Optional: Any excludes for files you don’t need to back up. Here, I’ve set BackupFilesExclude to ignore Music and Videos, since I also have those files on my PC.
Here is my configuration:
Why backup only those directories?
- /data/, for all installed applications’ apk files and their configurations.
- /mnt/asec/, for APP2SD-compatible apps’ apk files.
- /mnt/emmc/, because my tablet mounts additional internal storage there.
- /mnt/sdcard/, for obvious reasons.
Why not backup the root directory? Because it’s a rootfs, which is just tempfs. Even if you wanted to back it up, you can’t restore to it. You only need a few subdirectories.
Why not backup /system/? Because I haven’t remounted /system/ read-write, nor changed the firmware from the regular CyanogenMod install. For disaster recovery, I plan to reinstall CyanogenMod, then restore the lost apps and their configurations.
Once done with the Xfer settings, test it by starting a full backup of your Android device. If you get the dread “unable to read 4 bytes” message, check that your SSH authentication is actually working. My server ran the first full backup in 20 minutes, and now runs nightly in about one minute.
Aside: SSH logins on Android default to a minimal bourne-type shell. It has no colourisation and no tab-completion. If you plan on doing anything else from the command line, you may find it convenient to start bash immediately after login.
ssh -t root@192.168.0.100 'cd / ; echo ; bash'
-
Bummer that CyanogenMod 7 doesn’t support the Droid X2. Otherwise I would be rooting my phone right now. Have you had much experience with other rooting options?
-
Great How-to just got things working on my Nexus One with a fresh flash of CM 7.2 running my first backup now!
Thanks
PS taking your word for not being able to backup / so i just pain stakingly added all the root directories manually. Call me parinoid but, i would rather have to much instead of not enough when it comes to backups.
-
Pingback from Sauvegarde Android avec BackupPC on 2012-09-02 at 13:35 +00:00
-
-






6 comments
Comments feed for this article
Trackback link: https://www.tolaris.com/2011/06/13/backing-up-your-android-device-with-backuppc/trackback/